Friday, May 8, 2020
Thursday, May 7, 2020
Toll Group has been attacked by ransomware known as Nefilim
Toll Group has confirmed they suffered a ransomware attack for the second time in four months.
According to the company, Toll Group took the precautionary step of shutting down certain IT systems after unusual activity on some of servers was detected. Later, Toll Group confirmed the attack was a new form of ransomware known as Nefilim. Charles Ragland, security engineer at Digital Shadows, explains that “Nefilim is a relatively new ransomware variant that was first identified in March 2020. Notably, current reports suggest Nefilim uses exposed Remote Desktop Protocol (RDP) connections for infection. This attack vector has previously been used by ransomware variants like SamSam, where attackers would brute-force passwords for machines exposed via RDP. For attacks that target RDP, organizations should look to reduce their attack surface by disabling RDP on machines where it isn't necessary, use an RDP Gateway, and enable Network Level Authentication for RDP connections.”
"This is unrelated to the ransomware incident we experienced earlier this year. Toll has no intention of engaging with any ransom demands, and there is no evidence at this stage to suggest that any data has been extracted from our network. We are in regular contact with the Australian Cyber Security Centre (ACSC) on the progress of the incident," the company said.
In an update, Toll Group noted that they completed an important step in the restoration of IT systems with the full and secure reactivation of one of their core IT systems which underpins most of the company’s online operations. And as such, they are planning for business continuity and manual processes to continue into next week to keep services moving as thwork towards they e full and secure reactivation of the online systems.
The company added that they continue to work through the scanning and testing of servers which they will gradually and securely bring back online. In addition, Toll says, they have re-established external email into the company, and email access for Toll employees who operate on their cloud-based platforms is being progressively restored. Work is continuing on restoring remaining email servers.
Rui Lopes, Engineering and Technical Support Director at Panda Security, claims that, “When large companies are specifically targeted by hackers, their business can literally be under attack every day, so it’s no surprise that a second ransomware attack on Toll Group occurred. However, after the first attack, a thorough forensic analysis should have determined where security protections and protocols failed, and subsequently should have rolled out next-generation endpoint security on all endpoints. In the case of ransomware, lightning can strike twice, and there’s no grace period that’s honored before the next attack.”
Fausto Oliveira, Principal Security Architect at Acceptto, noted that the Toll Group is able to restore their operational environment from backup by using their Business Disaster Recovery plan. "It is also good that they acted swiftly and brought down affected systems, hopefully minimizing the spread of the ransomware."
On a less positive side, Oliveira adds, "we have an organization that has been affected for six days with all the financial and reputational consequences this incident brings not only to them but also to their customers and consumers. The fact that they have been attacked twice by what seems to be tailored ransomware opens the question of how is this possible, i.e. how did the malware manage to get into the organization and why weren't more robust processes in place to avoid this malware being dropped into the environment?"
Reading the analysis provided by TrendMicro, says Oliveira, the vector used to deploy the malware is either by the victim downloading the payload from a malicious URL or via a malware dropper. And in lack of greater detail it leads to three hypothesis, notes Oliveira:
- Either the executable payload was downloaded mistakenly by a user and it was not caught because web gateways are not being used or are misconfigured
- Some zero day dropper was used that exploits a vulnerabilities and allows the ransomware to be dropped into the production environment and the endpoint protection solution didn't detect the execution of the malware
- There is an surface of attack that is open and exploitable which wouldn't be the case given the previous incident.
"The first hypothesis can be addressed by reviewing existing security controls and establishing processes to change how executable payloads can be denied at the point of entry," Oliveira says,"The second hypothesis requires further analysis, however, some controls such as whitelisting payloads, OS monitoring tools and modern EDR tools, should have stopped the infection in its tracks, preventing it from affecting further assets. The third, if true, shows that there is more effort required by the Toll Group to perform a thorough review of the surfaces of attack open to external and internal actors and start using security controls such as micro segmentation and zero trust to avoid a repeat of this incident.”
Monday, May 4, 2020
Sunday, May 3, 2020
Friday, May 1, 2020
Thursday, April 30, 2020
Detect Intruders Using Canarytokens
#canarytokens Help you to detect if some intruders are poking around your network or accessing your #system #database #email.. #CyberSecurity #ethicalhacking #informationsecurity #data #privacy
Encrypt Your Data Without Leaking To Third Parties
Let’s get straight to the point. There’s a dark world out there in the wilderness of Internet. Taking some basic precautions like encrypting your data will give you enough immunity to deal with the unknown. So here we dive.
- Switch to communication platforms that offer encryption.
Encryption is ciphering your messages so that only the intended receiver gets the message. This is pretty basic now and I am guessing most of you are already using it. For those who aren’t, choose mediums that offer strong encryption like WhatsApp messenger, iMessage and Signal for text messaging, and Facetime, Firefox Hello, Google Hangouts and Signal for video calling. In the weaker side of this spectrum lies emails, phone calls and SMSing.
- Update your software.
Software developers work hard at ensuring you receive the best features while operating your device. They are constantly at it. So, update your software (keep away the lazy) to ensure you have the latest features added to your software. This will make sure that you are extra protected.
- Look for the lock.
Verify that the websites you are on use encryption before you give away your personal info. The websites that use encryption will have a tiny lock icon next to the web address. Next time, look for the lock.
- Gain some insight on online tracking.
Every website that you use tracks your activities to ensure you receive more of what you are looking for. Most of the websites asks for permission to do this. But others don’t. A simple answer is to use an extension that will help you see who is watching you. Try Mozilla Lightbeam, an add on that gives graphical data on who is scanning you.
- Use 2FA whenever possible.
Two-factor authentication is a go-to move for all you virtually aware people. For instance, requiring an OTP whenever there is a log in to your account will give you added level of security. Get started with your Gmail!
- For the nth time, get your passwords complicated.
As humans, we are gifted at complicating things. So, why not use the skill in password making? Get creative and complex. Bring in letters, numbers, special characters and experiment with cases. Let it be a Tower of Babel for hackers.
- Dump unused accounts.
Internet is no place to treasure things. If you are not using something, the best thing to do is do away with it. Delete accounts that you created on a whimsy but then left it to whimsies. To scare you a little, all your data stored in your unused data could be sold if kept untouched.
Wednesday, April 29, 2020
Adobe has updated their security patches for Illustrator , Magneto and Bridge
It's not 'Patch Tuesday,' but software giant Adobe today released emergency updates for three of its widely used products that patch dozens of newly discovered critical vulnerabilities.
The list of affected software includes Adobe Illustrator, Adobe Bridge, and Magento e-commerce platform, containing a total of 35 vulnerabilities where each one of them is affected with multiple critical arbitrary code execution flaws.
According to security advisory Adobe released, Illustrator 2020—one of the most popular designing software with millions of users around the globe—contains 5 critical code execution flaw, all existed due to memory corruption bugs in the Windows version of the software.
Digital asset management app Adobe Bridge version 10.0.1 and earlier for Windows operating systems have been found vulnerable to a total of 17 new flaws, 14 of which could lead to code execution attacks and are critical in severity—all discovered by security researcher Mat Powell.
The other 3 Adobe Bridge flaws are important information disclosure issues.
Besides these, Adobe today also released updates for commerce and open source platforms editions of Magento CMS that patches a total of 13 vulnerabilities—with 6 critical, 4 important, and 3 moderate in severity.
According to the advisory, all critical arbitrary code execution can only be exploited by a malicious authenticated user or an attacker with the compromised admin-equivalent account.
Though some of the important and moderate severity flaws don't require admin rights, an attacker still must need to have access to a low-privileged account to exploit those issues.
If you own an online store running over Magento, it is highly recommended that you upgrade your e-commerce website to the latest version of Magento as soon as possible.
Resource: Cybersafe News
Tuesday, April 28, 2020
WHO (World Health Organization) Confirms Email Credentials Leak
Washington Post had identified the group as one among several whose passwords and emails were dumped online and abused.
The World Health Organization this week disclosed that some 450 active WHO email addresses and passwords were leaked online recently amid a big overall increase in cyberattacks directed at its staff.
WHO is one among several groups working to fight the COVID-19 pandemic that have reportedly had their email addresses and passwords dumped online in recent days by an unknown entity. The others allegedly include the Gates Foundation, the US Centers for Disease Control and Prevention (CDC) and the National Institutes of Health, according to the Washington Post, which cited a report from the SITE Intelligence Group.
Some 25,000 email credentials belonging to these groups have been leaked online in recent days and are being used by far-right extremists and hackers to spread conspiracy theories related to the pandemic, the Post said, citing SITE Intelligence.
WHO is the first among the organizations in the Post report to publicly admit that email addresses and passwords belonging to its staff have been publicly leaked. In a statement, however, the global body said the leaked data does not pose any risk to current WHO systems because the data is not recent. But it does affect an older extranet that is used by current and retired WHO staff and by partners, the global organization said Thursday. "WHO is now migrating affected systems to a more secure authentication system," the statement noted.
WHO did not disclose from where or how attackers might have obtained the email addresses and passwords. But they are most likely from earlier data breaches, according to Colin Bastable, CEO at Lucy Security. "The common 'covid' nature of the organizations targeted strongly suggests that they are old credentials that have been bundled to take advantage of the current virus crisis," Bastable said in emailed comments.
The email credential leak is part of a broader increase in attacks targeting or involving WHO since the beginning of the coronavirus pandemic. According to the world health body, the number of cyberattacks targeting it is now five times more than the number of attacks one year ago. Scammers impersonating WHO staffers are increasingly targeting the general public in campaigns designed to divert donations meant for the COVID-19 Solidarity Response Fund to fictitious accounts, WHO said.
Numerous security vendors have reported a massive increase in phishing and other scams by attackers trying to exploit the global concerns around the pandemic to steal credentials, plant malware, and cause other mayhem. In many cases, adversaries have established malware-laden fake domains designed to take advantage of people looking for information related to the pandemic.
The increase in malicious activity has been so dramatic, in fact, that three Democratic lawmakers earlier this month demanded to know what the major domain name registrars were doing to prevent scammers from registering fake domains with COVID-19 related themes.
In a letter to the CEOs of eight domain registrars, the lawmakers wanted to know what these organizations were doing to establish the legitimacy of people and entities trying to register domains with names related to the pandemic. They also wanted to know what measures domain registrars had for identifying and removing domains that were being used for malicious purposes.
Resource: Darkreading...
Monday, April 27, 2020
GIF Image Have Attacked Microsoft Team Accounts
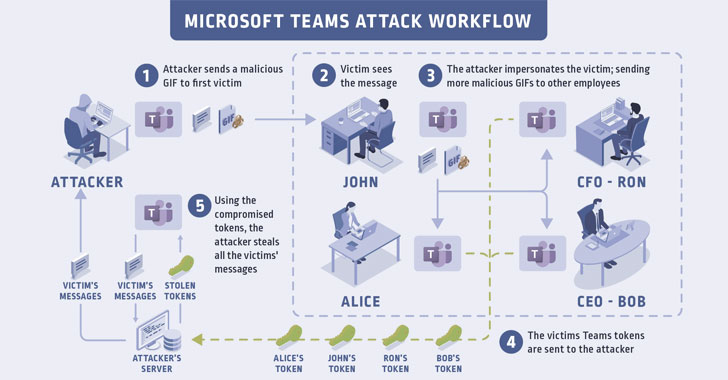
Microsoft has patched a worm-like vulnerability in its Teams workplace video chat and collaboration platform that could have allowed attackers to take over an organization's entire roster of Teams accounts just by sending participants a malicious link to an innocent-looking image.
The flaw, impacting both desktop and web versions of the app, was discovered by cybersecurity researchers at CyberArk. After the findings were responsibly disclosed on March 23, Microsoft patched the vulnerability in an update released on April 20.
"Even if an attacker doesn't gather much information from a Teams' account, they could still use the account to traverse throughout an organization (just like a worm)," CyberArk's Omer Tsarfati said.
"Eventually, the attacker could access all the data from your organization's Teams accounts — gathering confidential information, meetings and calendar information, competitive data, secrets, passwords, private information, business plans, etc."
The development comes as video conferencing software such as Zoom and Microsoft Teams are witnessing an unprecedented surge in demand as businesses, students, and even government employees across the world are forced to work and socialize from home during the coronavirus pandemic.
A Subdomain Takeover Vulnerability
The flaw stems from the way Microsoft Teams handles authentication to image resources. Every time the app is opened, an access token, a JSON Web Token (JWT) is created during the process, allowing a user to view images shared by the individual or others in a conversation.
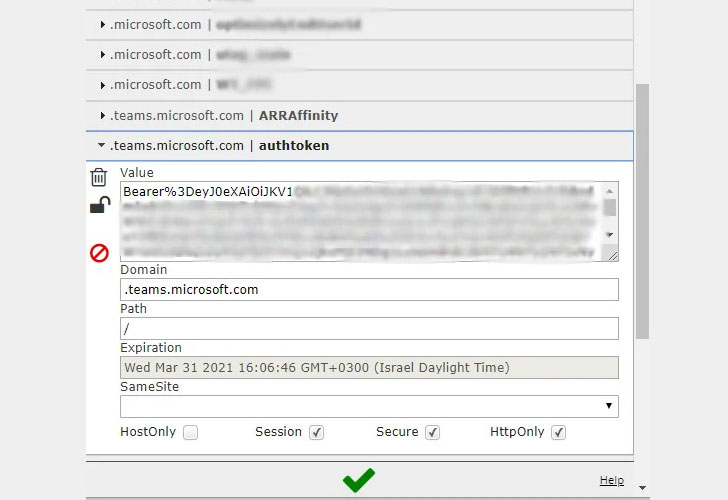
CyberArk researchers found that they were able to get hold of a cookie (called "authtoken") that grants access to a resource server (api.spaces.skype.com), and used it to create the aforementioned "skype token," thereby giving them unfettered permissions to send messages, read messages, create groups, add new users or remove users from groups, change permissions in groups via the Teams API.
That's not all. Since the authtoken cookie is set to be sent to teams.microsoft.team or any of its subdomains, the researchers discovered two subdomains (aadsync-test.teams.microsoft.com and data-dev.teams.microsoft.com) that were vulnerable to takeover attacks.
"If an attacker can somehow force a user to visit the subdomains that have been taken over, the victim's browser will send this cookie to the attacker's server, and the attacker (after receiving the authtoken) can create a skype token," the researchers stated. "After doing all of this, the attacker can steal the victim's Team's account data."
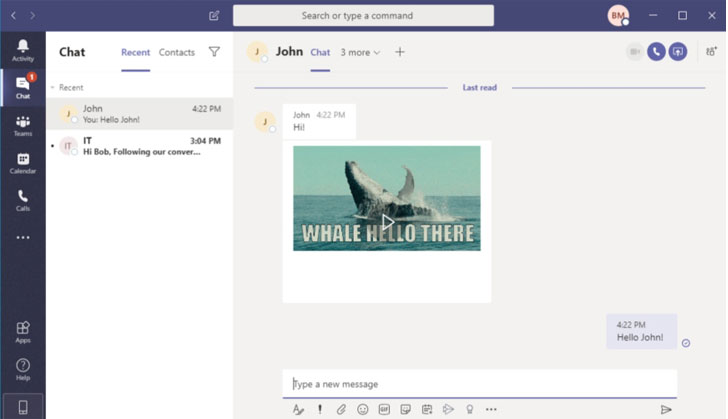
Now armed with the compromised subdomains, an attacker could exploit the flaw by just sending a malicious link, say a GIF, to an unsuspecting victim, or to all members of a group chat. Thus when the recipients open the message, the browser attempts to load the image, but not before sending the authtoken cookies to the compromised sub-domain.
The bad actor can then use this authtoken cookie to create a skype token and therefore access all the victim's data. Worse, the attack can be mounted by any outsider as long as the interaction involves a chat interface, such as an invitation to a conference call for a potential job interview.
"The victim will never know that they've been attacked, making the exploitation of this vulnerability stealthy and dangerous," the researchers said.
Videoconferencing Company-Themed Attacks on the Rise
The shift to remote work amidst the ongoing COVID-19 pandemic and the increased demand for video conferencing services have become a lucrative tactic for attackers to steal credentials and distribute malware.
Recent research from Proofpoint and Abnormal Security uncovered social engineering campaigns asking users to join a Zoom meeting or address a Cisco WebEx security vulnerability by clicking on malicious links that are designed to steal login credentials.
In the face of such emerging threats, it's recommended that users watch out for phishing scams and ensure video conferencing software is kept up-to-date.
Sunday, April 26, 2020
Saturday, April 25, 2020
Using an USB condom to protect from Juice Jacking
Most people associate a cyber-attack with things like phishing, exploitation of software vulnerabilities, RDP hacks, and sketchy websites hosting malicious code. This isn’t a misconception, but black hats have plenty of lesser-known tactics up their sleeve.
Would you expect a digital ambush when charging your smartphone via a USB power station in a public place? If the answer is “No,” then you are a potential target of juice jacking, a form of compromise that entails data theft through a hacked charging port. Even though the term sounds like fun, the concept behind it is a growingly serious issue for individuals and businesses.
Let’s take a dive into this phenomenon to understand how it works and whether it’s something to worry about.
Juice jacking 101
To execute a juice jacking attack, malicious actors take control of USB charging gear in airports, hotels, shopping malls, and other public spaces visited by numerous people, including business travelers. This hack becomes a launchpad for repurposing your charging session so that it serves as a channel of unauthorized data transfer.
If you take a close look at a standard USB connector, it has a total of four or five pins. Only one or two of them are required to charge the device and the rest are used for transferring information. You may have also noticed that when you connect your mobile gadget to a laptop or desktop computer via a USB port to charge it, the device that supplies the power will display a dialog offering you to move data back and forth. Whereas file transfer is typically disabled by default, a criminal who has access to the USB power station can enable it surreptitiously.
The attacker’s motivation is to steal numerous people’s data or to deposit malware onto devices. A particularly intricate scenario involves the use of a spyware app that mirrors the screen of the smartphone or tablet plugged into a hijacked USB port. This way, the hacker can remotely record passwords and PINs as they are being entered during the charging session.
This type of exploitation bears a resemblance to credit card skimming in a way, where crooks pilfer the details of debit and credit card inserted into ATMs. The similarity is that a malefactor exploits a real device in a public place – a cash machine or a charging station – by attaching a malicious component or by remotely enabling dodgy features.
Juice jacking poses a particularly high risk to businesses, and here is why. If an employee connects their company-issued smartphone to a hacked USB power station, perpetrators may get hold of proprietary information such as login credentials and corporate secrets. This data can be a source of industrial espionage, spear-phishing attacks, business email compromise (BEC) scams, and network-wide malware onslaughts.
How juice jacking splashed onto the scene
This attack vector was originally demonstrated by ethical hackers as a proof of concept. In 2011, a group of researchers from the Aires Security firm created a booby-trapped charging kiosk and installed it at the Wall of Sheep village, which is part of the Defcon event held annually in Las Vegas. On a side note, the Wall of Sheep is kind of a public embarrassment zone at the hacking conference where attendees with poor digital hygiene are shamed for their indiscretion. Although the kiosk would display a warning message every time someone plugged their mobile device into it, more than 360 people did it without a second thought in three and a half days.
Should you be concerned?
Even though security analysts don’t consider juice jacking a mainstream peril at this point, authorities have already given users a heads-up regarding the potential risks. An example is an alert issued by the Los Angeles County District Attorney’s Office in November 2019. The officials advised travelers against using public USB power charging stations as a countermeasure for malware attacks during the holiday season.
One of the reasons why juice jacking isn’t being flagged as a common threat so far is that there haven’t been any documented real-world cases and nobody has been caught red-handed yet. However, the threat isn’t as far-fetched as it may appear, with a few unverified incidents having been reported in the U.S. east coast area.
Two flavors of juice jacking
Juice jacking is a two-pronged threat. Based on the hackers’ tactics, experts single out the following sources of these attacks:
Public charging stations. When you connect your smartphone to a weaponized USB charging station, a remote attacker enables the data transfer mode and thereby retrieves your sensitive information or installs mobile malware behind your back.
Booby-trapped accessories. In this case, a charging device previously modified by criminals becomes an instrument for eavesdropping or malware injection. White hats have shown how this works. Back in 2013, enthusiasts from the Georgia Institute of Technology created a rogue charger they called Mactans, which allowed a hacker to infect a connected iOS gadget with harmful code.
Two years later, a researcher named Samy Kamkar masterminded a malicious Arduino-based device disguised as a regular USB wall charger. It allows a hacker to steal keystrokes from a wireless keyboard plugged into it.
What is the manufacturers’ response?
Tech giants such as Microsoft and Apple are aware of these vulnerabilities and try to address them. For instance, if you own a mobile device running iOS 11.4.1 and later, you will need to unlock it whenever it’s plugged into a USB accessory otherwise your gadget won’t communicate with that peripheral object. These efforts are certainly commendable, but staying on top of all the possible exploits is easier said than done.
Ways to keep your company’s devices safe
As previously mentioned, businesses are the “juiciest” targets of these incursions. By stealing employees’ login credentials, criminals can gain a foothold in the enterprise IT infrastructure and perpetrate effective scams or poison the network with malicious programs such as ransomware or crypto miners. To top it off, any illegally obtained business-critical information may be sold to a competitor.
Obviously, companies need to proactively defend themselves against this menace. Here are some best-practice tips to safeguard your organization against juice jacking attacks:
- Let your employees know about the threat
Be sure to complement the security awareness training for personnel with up-to-date information about juice jacking. Instruct your team members to refrain from plugging USB cables into public ports and emphasize the importance of using virtual private network (VPN) tools whenever they go online as an extra layer of protection against data theft.
In situations where charging a mobile device in a public place is a necessity, here are several worthwhile precautions:
- Use USB accessories from trusted manufacturers only.
- Abstain from using free USB charging cables that come with promo bundle kits, because they might be riddled with malware.
- Never use cables someone left connected to public USB charging kiosks.
- Decline data transfer requests that appear when you start a charging session.
- Provide employees with power banks
This one is self-explanatory. If you don’t want your staff to use potentially hijacked charging stations, company-issued power banks are a decent alternative that should do the trick. This way, your employees can charge on the go and keep their devices safe.
- Enforce the use of USB condoms
No matter how “naughty” it sounds, a USB condom is an effective way to stop any juice jacking attack in its tracks. It serves as a protective shield between your charging cable and a USB port in a public place. Essentially, it keeps the charging function active while blocking data from being transferred in either direction via the cable.
- Use charging-only cables rather than data cables
It doesn’t take a rocket scientist to understand why a power-only USB cable eliminates the risk altogether. It only engages the connector’s pin (or pins) required for charging and disengages the ones intended for data transfer – as simple as that.
- Use the “good old” AC socket where possible
Charging your smartphone via a traditional AC power outlet makes a juice jacking attack impossible. One of the caveats is that it may not be easy to find a spare socket. Furthermore, business travelers should keep in mind that there are quite a few different types of power outlets around the world. If you know your route, make sure you carry the right adapter with you.
The bottom line
Here’s some good news: juice jacking isn’t a widespread threat so far and isn’t as likely to be encountered in the wild as phishing or ransomware raids. However, researchers have shown the practicability of such exploitation and cybercriminals can definitely do the same. Given the ubiquity of mobile devices and the fact that people increasingly depend on them, the issue might escalate anytime soon.
Real-world hackers are constantly expanding their repertoire, and if there is a hype train, they won’t miss it. With that said, you should think twice before plugging your smartphone into a public USB charging station. Also, make sure your family, friends, and colleagues know what juice jacking is and how to stay on the safe side.
Subscribe to:
Comments (Atom)
Ping Command
Using #pingcommand utility to find #ipaddress of a target #domain , Find the maximum network frame size and emulate the #tracert. #C...
-
We should keep all three components equally in terms of it's security as if you prioritize any of it's component too much then th...
-
In network scanning, your first procedure will be to scan the target network to determine all possible open ports, live hosts, and servic...
-
Firebug was started 2005 and which helped to inspect, edit, and debug code right in the Firefox browser. It also let you monitor CSS, HTML,...